Introduction
Phishing Email Statistics: Phishing emails have solidified their status in 2025 as one of the most dangerous and hardest-to-target global problems for both individuals and organizations at large. A seemingly harmless fake email in your inbox is, in fact, a highly sophisticated, data-driven crime process that aims to trick, invade, and rob the user, usually resulting in huge financial losses.
The use of artificial intelligence by the attackers, along with advanced social engineering methods and very precise BEC (Business Email Compromise) campaigns, has transformed phishing from a mere nuisance into a global problem that costs billions of dollars. This article will present the trending phishing email statistics and their impact on the different industries.
Editor’s Choice
- In Q2 2025, the total number of phishing emails sent worldwide is estimated to be around 102 billion, which is a 22% increase compared to the previous year.
- North America accounted for the largest share of global phishing with 38%, followed by Europe (27%) and Asia-Pacific (21%).
- Phishing volumes in cloud-based work environments are 30% higher compared to hybrid or on-premise setups.
- The governments of 18 countries saw a 42% rise in attempted phishing attacks on critical infrastructure.
- The use of Phishing-as-a-Service platforms increased by 49%, making it easier for attackers with low skills.
- Early 2025 saw a 35% increase in phishing emails targeted at healthcare organizations, especially in scheduling and billing departments.
- Around 11% of phishing emails pass through basic email security checks like SPF and DKIM.
- Phishing emails that mimic the appearance of real logos and signatures get 19% more engagement.
- The impersonation of internal communication tools such as Slack and Microsoft Teams has increased by 32% in the financial sector.
- Domain shadowing attacks have recorded a 43% rise, while 14% of phishing messages are now using CRM platforms like Salesforce as their bait.
- Kits for phishing powered by AI are able to replicate even the most comprehensive stages of the login process, thus increasing the probability of stealing credentials by 23%.
- It is reported that 61% of BEC attacks use stolen employee credentials, and their exploitation is often through already existing email threads.
- Organizations that rely on payroll diversion scams are faced with a 22% increase in attacks, with healthcare and education being the most affected sectors.
- Companies with staff strength of more than 1,000 are two times more prone to being the victims of BEC attacks.
- The mean clickability rate of phishing among employees in 2025 is predicted to be 11.6% but it will go as high as 21% for messages that invoke urgency or are of an emotional nature.
- Young employees, that is, those below 30, are 34% more likely to fall for the phishing trap than their older counterparts.
- The retail sector is leading the pack as far as phishing click rate is concerned, at 15.3%, and this can be attributed to the high turnover of employees in that sector.
- The rate at which phishing emails that use company branding get clicked is increased by 11.5%, while the proportion of clicks coming from mobile users is more than 30%.
- Phishing with synthetic identities that rely on deepfakes and AI-generated personas is 45% tougher to detect.
- Notifications of phishing attacks through collaboration tools have gone up by 39% as hackers are moving beyond the traditional email method.
Industries Most Targeted By Phishing Attacks
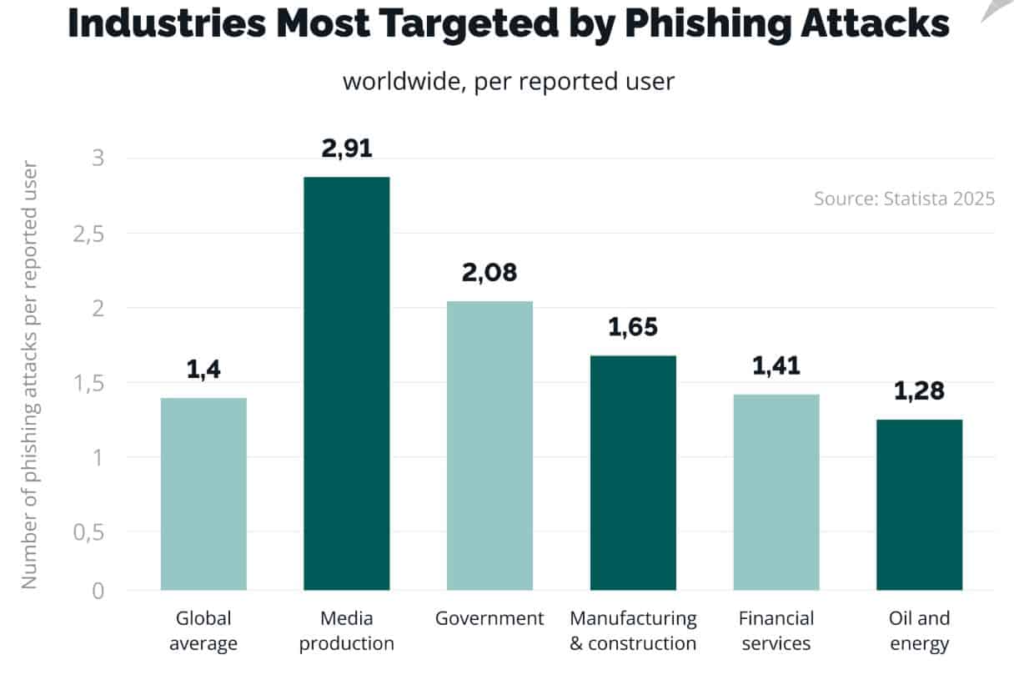
(Source: techmagic.co)
- AI-based phishing and social engineering scams have mainly targeted finance, healthcare, and government sectors since the latter started adopting AI for various applications.
- Cybercriminals targeted 92% of healthcare organizations in 2024, a slight increase from the 88% reported in 2023.
- The healthcare sector endured the heaviest losses from data breaches, with an average breach cost of US$9.8 million.
- Ransomware attacks were another major source of losses, as they resulted in almost 19 days of downtime in U.S. healthcare facilities, thus harming both patients and administrative processes.
- In the finance industry, 64% of institutions suffered BEC attacks in 2024.
- These attacks, on average, cost the institutions around US$150,000 per incident, which points to the increasing threat of AI-facilitated fraud in the financial industry.
Global Volume Of Phishing Emails
- By the second quarter of 2025, around 102 billion phishing emails were sent out globally, marking a 22% increase compared to the previous year.
- The largest portion of the phishing email market goes to North America at 38%, with Europe and Asia-Pacific following with 27% and 21%, respectively.
- The phishing problem is very serious in cloud work environments, where the volumes are 30% higher than those in hybrid or on-premise systems.
- In early 2025, government agencies in 18 countries noted a 42% increase in phishing attempts aimed at the vital infrastructure.
- The demand for Phishing-as-a-Service platforms on the dark web increased by 49%, thus making it easier for less-skilled hackers to do phishing campaigns.
- Phishing was the most prevalent among healthcare organizations in the first quarter of 2025, with a 35% increase, especially for those who were involved in patient scheduling and billing.
- During significant global events, phishing emails rise sharply, and in the regions affected, the increase can be as high as 68%.
- The share of mobile users receiving phishing emails has grown to 28%. Detection and downfall of phishing campaigns take an average of 96 hours, and in 2025, 29 attempts per user monthly are found by spam filters.
Email Spoofing And Brand Impersonation Rates
- Phishing emails continue to be dominated by Microsoft, Amazon, and Google as the brands most often impersonated.
- In 2025, 72% of phishing schemes resorted to brand spoofing to gain credibility.
- Currently, approximately 11% of phishing emails manage to bypass basic email security checks, e.g., SPF and DKIM.
- Scams that include fake logos and realistic signatures generate 19% more engagement than plain-text scams.
- In the financial services sector, there was a 32% increase in phishing emails impersonating internal tools such as Slack and Microsoft Teams.
- Domain shadowing—utilizing subdomains on legitimate websites for phishing—has grown by 43% annually.
- Close to 14% of phishing emails impersonate trusted CRM platforms like Salesforce to extract login details.
- The number of phishing emails impersonating LinkedIn rose by 56% during the first half of 2025.
- Government agencies like the IRS and DMV are also victims of impersonation, especially around tax season.
- Attackers can now use AI-based capacities to replicate entire login pages, which hampers the detection of the attack and leads to a 23% increase in stolen credentials.
Number of Phishing Emails Sent Worldwide
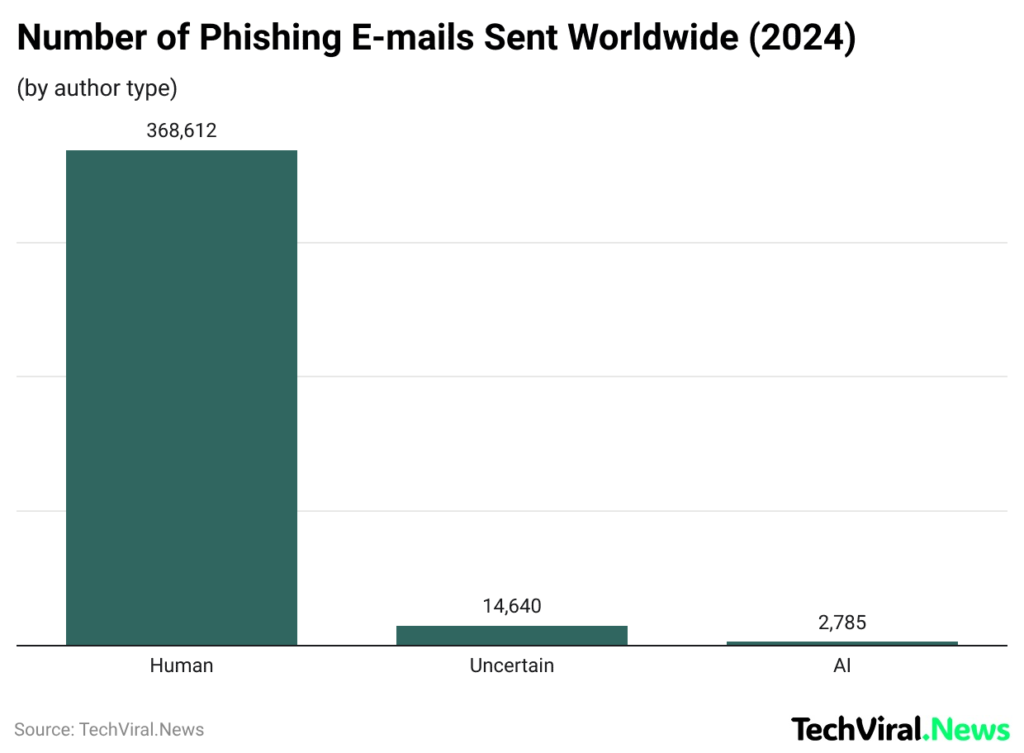
(Reference: techmagic.co)
- The human attackers occupy a very significant part of the overall panorama, as human attackers account for an overwhelming majority.
- Approximately 368,612 phishing emails are accounted, so it is clear that the majority of phishing activities are humans absolutely fueled and driven rather than automated alone.
- From all the emails, nearly 14,640 are untrusted, which means there were cases where the origin was left doubtful, or indeed no clear identification could be made.
- Very low accounts, close to just about 2,785, in total have been noticed in relation to the plus sources pointing specifically to AI-generated phishing emails.
- This suggests that AI-based phishing, while being the new thing, is still a small player in the game compared to the already established human attackers, since it gets to see only a small fraction of the total human attacks.
Phishing Trends In Business Email Compromise (BEC)
- Phishing in the form of BEC is predicted to account for 28% of total financial losses due to phishing in 2025.
- Such types of attacks are very expensive, and each incident averages about US$187,000 in losses for the victim company.
- The impersonation of vendors is the tactic that has grown the most; it is now 41% more compared to last year’s figures.
- BEC attacks now mainly(61%) consist of the usage of stolen employee login credentials, which makes the attackers act as if they are internal people and thus draws on internal email exchanges.
- Phishing by replies has climbed by 36% and has become thrice as successful as the old method of sending fresh, unsolicited scam emails.
- Payroll redirection cons are on the rise by 22%, especially in the education and healthcare sectors. Roughly half of BEC attacks are directed at the top managers, taking on the appearance of either the CEO or the CFO.
- In the first quarter of 2025, law firms and accounting companies reported a 29% increase in BEC incidents, and companies with more than 1,000 employees are twice as likely to be a target.
Employee Click-Through And Engagement Rates
- On average, employees of 2025 apply to get infected with phishing emails in the proportion of 11.6% of the total emails.
- Urgent or emotional subject lines attract the maximum engagement, and hence, the click rates go up to 21%.
- The youngest lot of workers, i.e., those under 30 years, is prone to clicking phishing links by 34% compared to those over 50 years.
- Retail has the highest industry click rate at 15.3%, which is mainly because of the constant ups and downs in the staff.
- If the employees are to be given the month’s training that covers the same ground as the quarterly, then those who have had the monthly training are going to respond less carefully than those who have had the quarterly.
- Phishing emails that pretend to be internal notices or policy updates saw an increase in clicks by 19%, which indicates that the branding for the internal communication is trusted heavily.
- Working from home does make workers twice as likely to fall for phishing emails, mainly the ones that simulate productivity tools.
- Moreover, the use of company logos has been found to lead to an increase in the click rate by 11.5%.
- Meanwhile, over 30% of the clicks on phishing links are from mobile users, while companies implementing gamified security training experienced a 48% reduction in employee click rates within three months.
Recent Developments In Phishing Email Tactics
- 2025 is the year that witnessed a 48% increase in phishing emails hiding texts inside the pictures as the attackers are attempting to outsmart the email security scanners.
- The phishing attacks that utilized the HTML attachments soared by 64%, with emails presenting very realistic-looking forms set for stealing the users’ login credentials.
- The trust-building days or weeks in conversational phishing are counted as one of the most deceptive phishing IT practices and are increasing by 31%.
- Cybercriminals are resorting to synthetic identities created from deepfake images combined with AI-generated personal stories, thus making these scams 45% harder to detect.
- Time-delayed malevolent links that turn dangerous hours after delivery and are now 32% more effective at escaping real-time security checks.
- Phishing has become a global issue, and it is no longer restricted to email, as it has been done through collaboration tools like Slack, Microsoft Teams, and Notion, which have seen a 39% increase in phishing attempts.
- The use of new techniques, such as fake CAPTCHA checks that give the impression of having gone through the normal process and consequently being very polished, AI-generated emails that are indistinguishable from the human-written ones, and sound even more professional, are among the new methods.
- The use of advanced URL tricks with redirecting and proxying is now found in 27% of phishing emails. Attackers have also started using phishing simulation tools that are available on the market to check and enhance their scams.
Conclusion
Phishing Email Statistics: Phishing emails are still one of the most significant and fastest-changing cyber threats in 2025. With the number of global phishing emails going into billions and the use of AI, brand impersonation, to sophisticated social engineering by the attackers, both people and organizations are more liable to risk. The industry sectors of healthcare, finance, and government bear the brunt of the attackers through very high financial and operational impacts.
It is still true that human-based attacks take the lead, but AI-assisted ones are slowly coming up. These patterns point to a greater need for robust email security, frequent employee awareness training, and agile defenses so that the financial losses caused by phishing campaigns are reduced, the sensitive data is protected, and the organizations stay one step ahead of the ever-sophisticated phishing attacks.
FAQ
Phishing emails are more dangerous in 2025 due to the fact that attackers are employing artificial intelligence, employing sophisticated social engineering, and highly focused BEC campaigns. These techniques make the emails look very real, personalized and difficult to catch, thus raising the likelihood of financial loss and data theft.
The healthcare, finance, and government sectors are the main ones attacked. Healthcare has to deal with very high breach and operational downtime costs, financial organizations are the victims of BEC attacks frequently, and government departments are under attack because of the sensitive information they handle and the infrastructure they control.
By mid-2025, the global phishing email volume was about 102 billion emails per year, which is a 22% rise compared to the previous year. The growing use of mobile devices and cloud-based work environments has been a major factor behind the rise of phishing as a global issue for the future.
BEC is a type of phishing attack where the perpetrator impersonates a trusted business partner, like a top executive or a vendor. In 2025, BEC caused losses equal to 28% of total phishing fraud, with US$187,000 as an average per incident due to tricking the financial system and rerouting the payroll.
Companies should keep an eye on image-based phishing, HTML email attachments, conversational phishing, the use of synthetic identities created with deepfakes, phishing in collaboration tools, and email written by AI. All these methods are meant to go unnoticed by security systems while being very convincing to the users.
